Recently, the cases that students have been exposed to telecom fraud have aroused widespread concern in society. After investigation, China Youth Daily Zhongqing Online reporter found that a large number of students’ information was sold at a marked price on the Internet, but mobile phone cards and bank cards that should have been handled in real names could be easily bought without registration.
High school students’ information 100 yuan 1000.
China Youth Daily Zhongqing Online reporter searched related keywords on social platforms and found hundreds of QQ groups related to "information trading", many of which were directly named as "student data trading" and "bank data information trading". After joining some QQ groups, the reporter found that there are buyers and sellers in these groups, with the number ranging from tens to hundreds. From time to time, some people in the group posted news such as "selling the latest student data information, chatting privately" and "buying student information in XX".
The reporter posted a message in the group asking for students’ information. Soon, many people took the initiative to contact the reporter and asked which stage and region students’ information was needed. The reporter asked the seller if he had any information about Henan high school students, and the seller showed his database to the reporter in the form of screenshots. On the screenshot, the reporter saw that there are 18 Excel files, except one named "Yongcheng" (a county-level city under the jurisdiction of Shangqiu City, Henan Province — — Reporter’s note), the other 17 are all named after cities in Henan Province. According to him, it contains the information of senior high school students in various regions, with an offer of 1,000 in 100 yuan.
Another seller also took the initiative to contact the reporter. He said that he had information about more than 30,000 failed students in Henan. The reporter raised doubts about the authenticity, and the other party said, "I have been in this business for several years." After negotiation, the other party finally gave two screenshots of the complete information of 25 students, under the condition that the reporter proposed to buy in large quantities immediately if it could be verified for free. The students’ names, gender, school, home address, contact information, parents’ names and contact information are all available on the screenshot, and the level of detail is surprising. The seller’s quotation is 1,000 pieces of information for ordinary high school students in 100 yuan and 1,000 pieces of information for "sliding" students and art students in 200 yuan. The seller also assured reporters that the "data provided are all the latest".
The reporter tried to call a number of students in the screenshot continuously to verify that all the information given in the screenshot was true, but the students and their parents were shocked after learning that their information was leaked, and they didn’t know when their information was leaked.
So where did the information provided by these sellers come from?
It is understood that hackers have become a key part of the industrial chain of personal information underground transactions. Yang Wei, the head of Beijing Zhongan Tianxia and a well-known "white hat" and "301", has done special research on the personal information security of candidates. In an interview with the media, he said: "This information is very valuable. Some people buy it and some people sell it. Since someone downstream is willing to spend money, there will naturally be hackers to attack these targets. Hackers illegally obtain this information, and after getting the data, someone will take over. There are also a large number of two-way traffickers, earning the difference in the middle. "
According to the 2015 China Internet Security Report released by a network security company, the information leakage loopholes in domestic websites can lead to about 1.15 billion pieces of personal information leakage, accounting for 43.7% of the total information that may be leaked by enterprises/personal websites (2.63 billion pieces). Among them, IT/ Internet websites may leak the most personal information, which is 523 million, followed by 240 million medical and health websites, 197 million telecom operators, 110 million financial websites, 54.18 million automobile transportation websites and 24.62 million education and training websites.
Some insiders said that many websites are too simple in password design and have numerous security loopholes, which makes them easy to be attacked by hackers.
In addition to hackers, some insiders of education and training institutions will also actively sell candidates’ information. On August 24th, Haidian District People’s Court of Beijing sentenced a case in which employees of a training institution sold information about students and their parents. Six people, including Yang and Xu, who work in training schools and education companies, illegally obtained and purchased more than 2 million pieces of information about students and parents. In addition to sending advertisements to parents at fixed points, they also sold them on online platforms such as Jiji.com and 58 City. Six people, including Yang and Xu, were sentenced by the court to one year, three months, six months and one year’s probation for the crime of illegally obtaining citizens’ personal information.
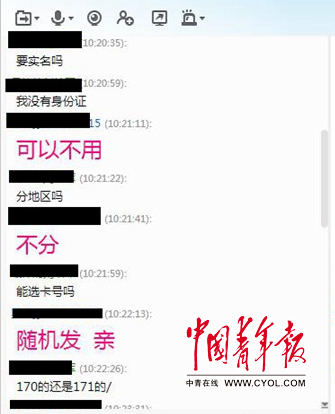
Sections 170 and 171 have become the hardest hit areas for non-real-name mobile phone numbers.
With the detailed information of the victim, fraudsters can implement "precise fraud" against the victim. In many telecom fraud cases, the phone numbers used by scammers are mostly paragraphs 170 and 171. Why do scammers favor the phone numbers of these two numbers?
It is understood that paragraphs 171 and 170 are both virtual operation numbers. Virtual operator contracted the right to use part of the communication network from the three basic operators of China Mobile, China Unicom and China Telecom, and then sold it to consumers through its own billing system, customer service number, marketing and management system. However, virtual operator’s control of agency channels is not strict enough, and the state’s binding force on virtual operator is relatively low. Therefore, paragraphs 170 and 171 have become the hardest hit areas for non-real-name mobile phone numbers, and they have been used by fraudsters.
The reporter contacted a merchant on Taobao with the service scope of "170, 171 calling card recharge". Knowing that the reporter was going to buy a non-real-name registration system phone card, the customer service staff introduced a Unicom phone card called "Yuanteka", and made it clear that this phone card does not need real-name registration, and each phone card costs 33 yuan.
The reporter asked how to pay, and the other party gave a link to the shop selling the card cutter, and specially reminded the reporter to adjust the quantity of goods to "21 pieces". The reporter clicked on the link and found that the card cutter in this store was priced at 1 yuan per piece. When the reporter adjusted the purchase quantity to 21, the payment page automatically became 33 yuan. The reporter’s investigation found that the normal unit price of the card cutter on the market is above 5 yuan. The reporter asked: "If you really want to buy a card cutter in 1 yuan, do you sell it?" The customer service staff replied: "Not for sale."
In addition to finding non-real-name registration system phone cards on the e-commerce platform, the reporter also found many QQ numbers selling non-real-name registration system phone cards on Baidu search. The reporter added one of them as a friend and found that in this account space, there are many daily business situations, and many pictures are taken of the whole box of shipping phone cards.
According to the other party, the calling card he sells has no monthly rent, no roaming, no minimum consumption, and no real name registration is required. The reporter asked: "Will it be stopped because it is not registered?" The other party answered "no" with certainty because "the company has been registered".
In the QQ group selling information mentioned above, the reporter also found that not only some people buy and sell student information, but also some people publish the news of selling bank cards, and in the news, they write "Money laundering, anonymous collection and transfer leave no trace". The price offered by the seller is "bank card+copy of ID card+reserved mobile phone card+390 yuan with account opening receipt", and 100 yuan will be added if necessary.
The card seller said that using this bank card transaction, others are "absolutely unable to find it". The card seller also said that he can provide accounts of major banks, "I can provide as much as you need."
The card seller said that he was just a middleman, and the bank card was bought from others, and all he earned was the difference. However, he was also very careful in his conversation with reporters. He said that he was "frightened by TV reports these days".
Some police said that one of the reasons why many telecom fraud cases are difficult to solve is that the bank cards used by scammers are not opened by themselves, but purchased online. Even if the public security organ finds the account holder, it will only catch the card seller, not the liar himself.
Eliminating telecom fraud requires joint efforts.
In view of the question that netizens generally questioned why the swindler’s account could not be frozen quickly after the victim was cheated, Zhang Kai, a policeman with 17 years’ police experience, told the reporter that the freezing procedure requires the police to make a record of the victim, collect the evidence of being cheated, and then report the inquiry and freezing procedure after the reported case is approved. This process takes at least three hours, and it usually takes only a few minutes for a liar to transfer all the money transferred by the victim. By the time the police arrived at the bank for freezing, the money had already been transferred away. It is understood that at present, the network server of telecom fraud, the location of criminal suspects and the stolen money are often abroad, and occasionally the stolen money is not transferred abroad, and the money cheated by the victim will be quickly decomposed, transferred many times and withdrawn from various places within half an hour.
Since telecom fraud is a "non-contact" crime involving many fields, it needs the joint efforts of many departments to combat and prevent telecom fraud.
On March 4th this year, the China Banking Regulatory Commission issued the "Notice on Matters Related to the Banking Industry’s Fight against and Governance of New Crimes in Telecommunication Networks", which made a comprehensive arrangement for the banking industry’s fight against and governance of new crimes in telecommunication networks: banking financial institutions are required to strictly manage the real-name system, make full use of technical means such as online verification of ID cards, and carefully examine the identity documents of the handlers; At the same time, the number of cards opened is strictly limited, and each person can open no more than 4 cards per line in principle. In the notice, the CBRC also asked banking financial institutions to comprehensively sort out and improve their business processes, improve the level of internal control, effectively strengthen the safety management of bank cards, constantly strengthen industry self-discipline and strictly implement social responsibilities.
On April 9 this year, the Ministry of Industry and Information Technology responded to the media that it had urgently interviewed three virtual operator companies to solve the problem of lax implementation of telephone real-name registration system, and ordered the enterprises to rectify immediately, and suspended the allocation of new code number resources to these three virtual operator companies, and would not open them until the rectification was in place.
In addition to government departments, online search engine service providers are also duty-bound.
On August 22, Tang Xuelian, who lives in Shenqiu, Henan Province, found a refund phone number from Baidu in order to return the train ticket booked online, and was cheated out of 60,000 yuan step by step. That’s the life-saving money she raised everywhere to see her son with severe cerebral palsy.
After Tang Xuelian was cheated, Baidu issued a statement saying: "At present, some criminals use search results to automatically capture the characteristics of massive third-party website information, and make links containing false information rank high on the search results page through illegal acts such as machine clicks, so as to increase the probability of netizens clicking and take the opportunity to commit fraud." In this regard, Baidu will "continuously strengthen the anti-cheating system and strengthen manual investigation and intervention to crack down on such behaviors and prevent netizens from mistakenly believing false information".
Some experts suggest that in order to eliminate telecom fraud, besides government supervision, enterprise self-discipline and social supervision, relevant state departments and the media should also strengthen the popularization of public safety awareness. At the same time, the public should constantly improve their own quality and discriminating ability. Don’t open links to strange websites in SMS and WeChat at will, and don’t trust strangers’ calls involving transfer requirements.
关于作者