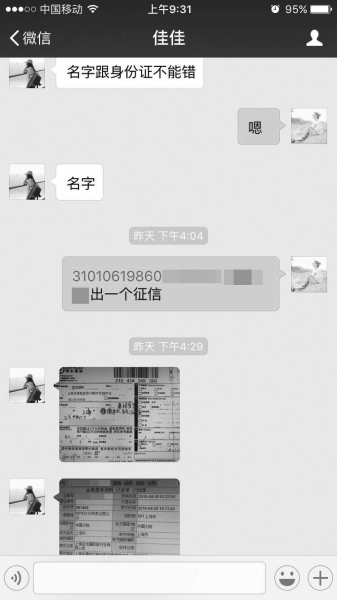
"A set of 100 yuan, including photos of the front and back of the ID card, photos of holding the ID card and videos of nodding, shaking your head and opening your mouth." On some social platforms and websites, many sellers clearly priced the face recognition video, and also guaranteed that the verification video sold could pass the verification process of most APP platforms.
threemoon30SolsticefourmoonfiveOn the day, the Beijing News reporter found that most of these underground black goods transactions were hidden inQQIn the group and overseas websites, among themQQGroup names mostly include keywords such as "face-crossing" and "recognition technology", so as to facilitate buyers to retrieve relevant information.
existAPPIn the black production of platform face verification, a set of verification videos with a price of 100 yuan belongs to "high quality" products, because the dynamic verification videos recorded by real people are used, and the verification pass rate is high. There is also a low-cost face authentication method, that is, using dynamic software to make face photos into "dynamic videos" and cooperating with "plug-in" software for verification.
"A low-cost set costs only a few dollars, and if the demand is large, it can even be as low as0.5Yuan a set. "A seller said that the success rate of face dynamic verification mainly depends on the degree of detail in the dynamic processing of photos, but the video recorded by real people can definitely do it.100%Yes.
Regarding the sale of face recognition information, Zhao Zhanling, a lawyer of Beijing Yunjia Law Firm, said that according to the Civil Code, citizens have civil rights to personal information, and illegally collecting and selling other people’s information without their consent would constitute civil infringement. The facial feature information of a person is the information that can directly identify the true identity of a specific natural person, which belongs to the category of personal information. It is suspected of violating the law to buy and sell personal information without the consent of the user.
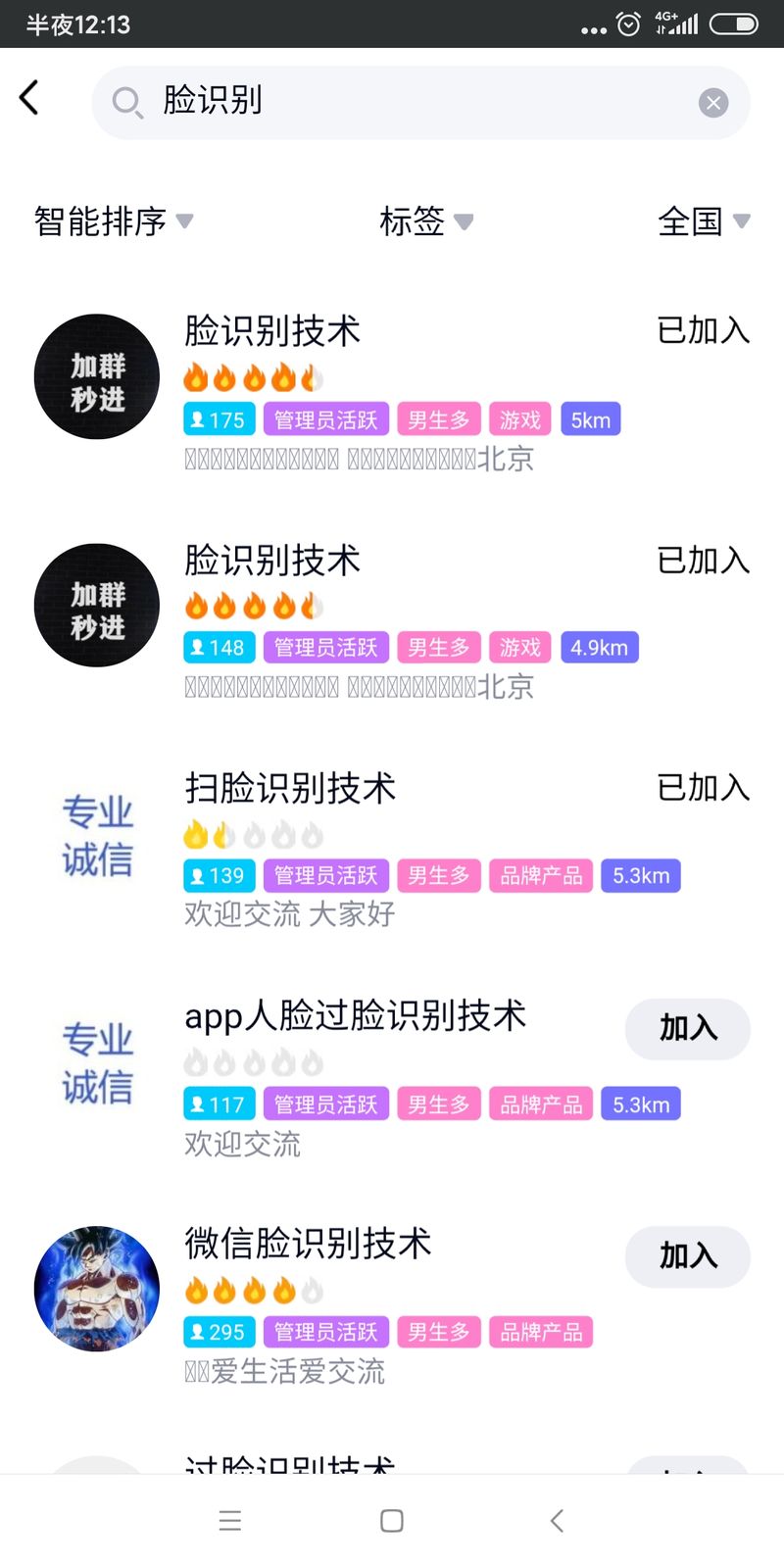
In QQ group, searching for the keyword "face recognition" will lead to many groups selling black goods. screenshot
"keep pace with the times" black goods trading
When registering for face verification in Weibo, Ms. Zhang was reminded that her ID card information had been registered, but she had not downloaded and used Weibo before.
Ms. Zhang consulted micro-blogging service and learned that if you sweep your face and register for Weibo, you will be prompted."This ID card has been bound to other accounts" or "ID card usage exceeds the limit" because the ID card has been bound to other accounts. At present, an ID number can be bound.2Weibo account, when the number of accounts bound with ID number reaches the upper limit, the current ID number can no longer be used for verification.
"My information must have been leaked." Ms. Zhang said that she usually pays more attention to the protection of personal information. The ID card has not been used anywhere except for going to school, getting a bank card, calling card, staying in a hotel and buying a ticket.
Ms. Zhang’ s experience is not unique. Many netizens have posted that they are registering in Weibo.QQ, WeChat official account, etc., found that personal identity information was stolen.
With the increase in the number of personal information being fraudulently used, network-related feedback and complaints have also increased, followed by majorAPPThe security verification upgrade of the platform takes dynamic face recognition as the security verification method. existAPPIn the iteration of platform security verification and upgrade, practitioners of this black industrial chain are also taking advantage of loopholes to "study" how to solve this "dilemma". With the development of Internet real-name registration system, this black goods interest chain has been upgraded from collecting and selling names and ID numbers to collecting and selling hand-held ID photos, face videos and photo dynamic processing software.
A black seller who sells personal information in the dark net introduced a set of photos of the front and back of ID cards, photos of holding ID cards and videos of people nodding and shaking their heads.100Yuan, a large quantity can be discounted, if you buy it at one time.100Set, the price can be lowered to10A set of yuan, "if the quantity is small, it is really not cheap, and the cost of collecting this information is also high."
Then, the other party sent two videos of opening mouth, blinking, nodding and shaking head recorded by others, saying"These are videos recorded by real people, verifying most of them.APPNo problem, it is higher than the dynamic video pass rate of photo processing. "
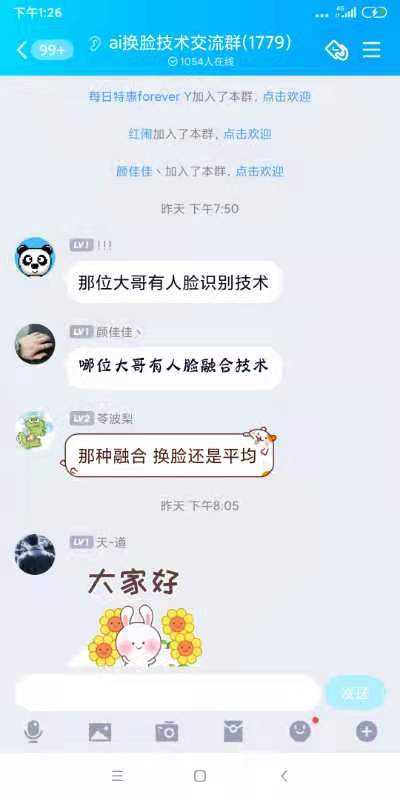
In a QQ group of more than 1,700 people, new people join every day to buy face recognition verification technology. screenshot
Most of the live verification videos come from "online part-time job"
A number of black sellers said that their development included borrowing money and making money on foot.APPThe information it sells comes from users downloading and registering these.APPCollected at the time, "most of these people are factory workers, and some network part-time workers."
However, these networks brush up part-time workers and don’t know what they are doing.APPWhen authenticating the list, it will reveal privacy.
Ms. Bai, from Shanxi, told the Beijing News reporter that she started to do some online part-time jobs such as brushing bills six months ago. Sometimes when the amount of brushing bills is limited, she will do some.APPA list of certifications.
Ms. Bai said that these orders need to scan the QR code provided by the other party to download.APPThen carry out real-name authentication. Most of the real-name authentication processes will allow uploading photos of the front and back of the ID card and face recognition, and then the registration will be successful. A list is probablyfiveYuan Dynasty (1206-1368)-15Yuan, some certification requirements are complicated and the price will be higher.
In the part-time billing, some only need to upload their names and ID numbers, so that each billthreeYuan, the price of face recognition may be more than ten yuan. Ms. Bai said, yesAPPIn face authentication, it will be easier to blink and shake your head a little, or the face will be closer.
"I didn’t expect anyone to collect personal information in this way, and I have never heard of anyone collecting dynamic videos of face recognition." Ms. Bai said that she just started to pick this up.APPWhen I registered the list, I hesitated when I encountered the verification of identity and face information, but later I felt that everyone in the group was taking orders, and I didn’t hear anyone say anything was wrong, so I started to do so.
The data leakage caused by part-time billing certification should be considered a minority. There have been media reports, there are80%The disclosure of personal information data is caused by employees within the enterprise.
Many black vendors also recognize this statement. Some vendors revealed that most of the photos of hand-held ID cards circulating in the market today were leaked during the brutal development of microfinance platforms and companies, and some of them were collected from various industries. This kind of information transaction and use will not be found under normal circumstances."At that time, many people borrowed money and didn’t pay it back. The platform took out this information and sold it. It was quite expensive at first, and now it is cheaper to resell it layer by layer."
In addition, today’s daily useAPPFace information needs to be recognized and collected on occasions such as entering and leaving stores, and some people collect information in the name of face recognition technology development and system testing.
In the network, the Beijing News reporter noticed that someone posted information about recruiting information collectors. The job content is to collect ID cards and face information in the countryside, and edible oil, pots and other commodities can be given as gifts.
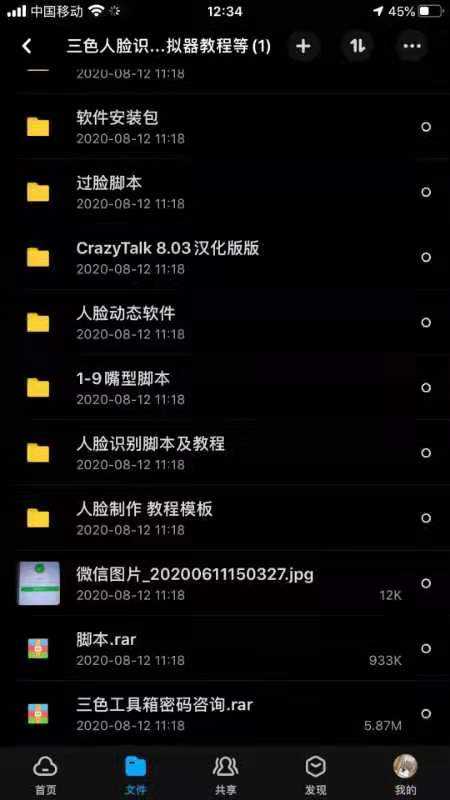
A face recognition verification data package sold by a black manufacturer, including software and tutorials. screenshot
"Four-piece set" of black production circle
Compared with real-life video recording, it is cheaper to dynamically process the face in the photo to form a verification video through software.
threemoon31On the day, the Beijing News reporter passedQQGroup search by conditions, enter keywords such as "face" and "recognition technology" in the search box, and there will be many correlations.QQGroup. Reporters joined at random.sixindividualQQGroups find that members in these groups are from100Yu ren Dao1700The rest of the people wait, and new members join from time to time.
QQIn the group, from time to time, some people publish information about selling micro-signals and face-changing software, and at the same time, some people are consulting how to dynamically process the people in the photos and verify them through face recognition.
In addition, after the Beijing News reporter joined the group as a person who needed to buy face authentication technology and software,threeWithin an hour, many black information sellers added friends to reporters to understand the needs.
These black sellers said that they sell software such as photo matting and dynamic processing to make the characters in the photos open their mouths, blink, shake their heads left and right and nod up and down. After that, open it through a specific mobile phone."Plug-in" for face recognition, "We generally use it to verify WeChat,QQThere are more momos, and other software can also verify faces. "
threemoon31A merchant engaged in the sale of black goods was in hisQQSpace release news said that due to the upgrade of WeChat security verification, it has been unable to pass face recognition verification for the time being, and I am studying ways.fourmoonthreeThe merchant said that he had overcome the new security verification and could take orders.
In addition, these merchants also sell positive and negative photos of ID cards, photos of hand-held ID cards and photos with faces, which are commonly known in the black production circle as"Four-piece set", the price of each set is in0.5YuanzhithreeYuan is not equal.
When asked about the source of these photos, merchants began to be cautious during the chat. Finally, the Beijing News reporter said that there was a large demand for four-piece information, and a seller said that someone was specially responsible for collecting it, and he bought it from others and then sold it.
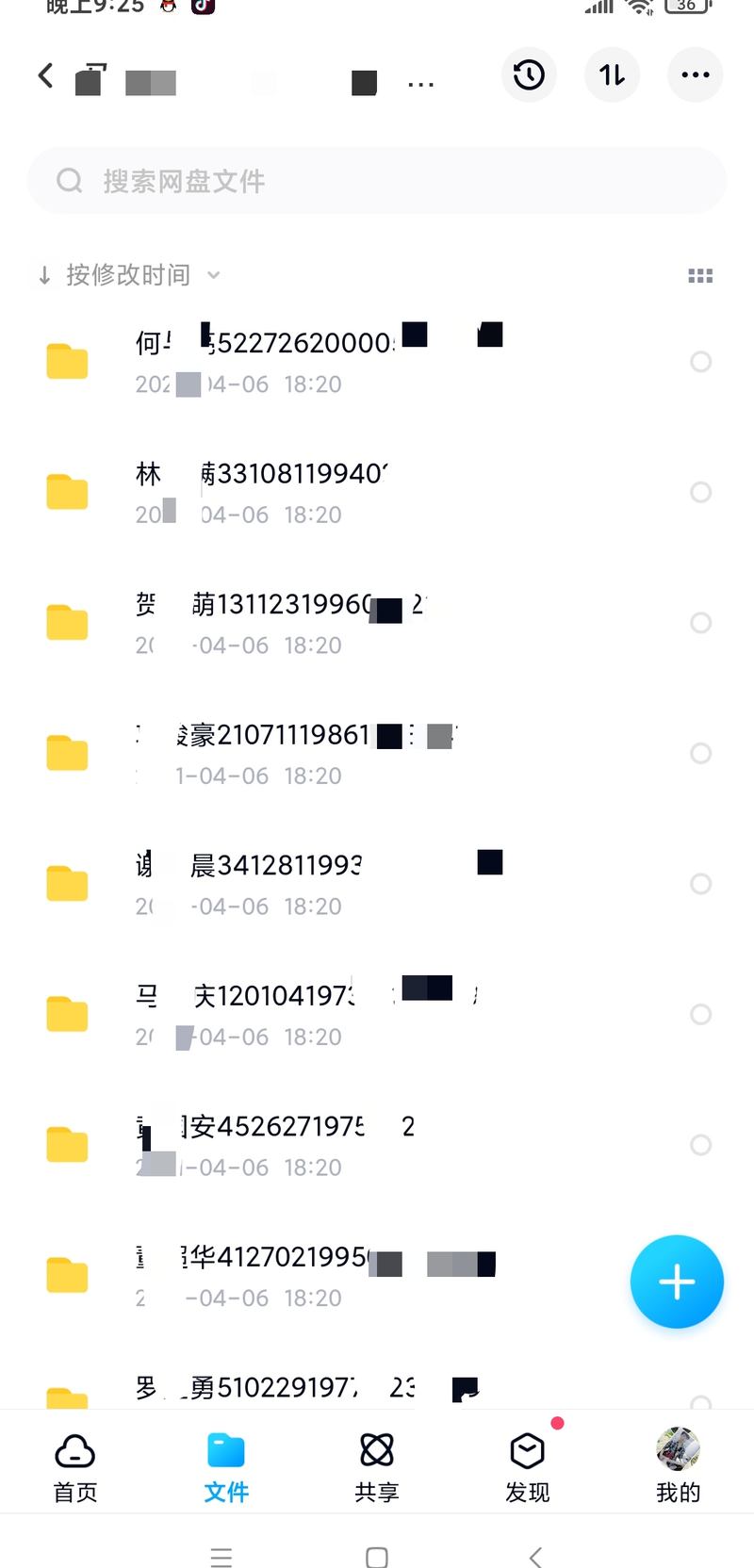
Personal information sold by black sellers, including ID numbers and photos. screenshot
Open "plug-in" software for face recognition
Whether it’s real-life video recording or photo dynamic processing, after completionAPPThe important tools for face dynamic verification are mobile phones and plug-in software.
The Beijing News reporter learned from asking black sellers that they spent money on second-hand trading platforms.200You can buy a second-hand brand with more than one yuan.R9Mobile phone, and then insert the brush package into the mobile phone.
partAPPIn the process of face recognition and verification, the screen will turn into red, yellow and blue to verify the brightness of the face, but the verification can also be completed by using relevant plug-in software.
"The purpose of brushing the mobile phone is to gain more rights to operate the mobile phone." For the principle of face recognition verification after photo dynamic processing, two black sellers said that whenAPPWhen you need to verify the face through the camera, cover the camera with your hand, and the "plug-in" of the mobile phone will start. By modifying the relevant data and settings, the dynamic face video prepared in advance will be imported into.APP, the authentication is completed.
"The pass rate of live-action videos is definitely high. The photo processing depends on talent. There is no guarantee that you can pass every verification. It depends on whether the dynamic video of your face is detailed. If the first verification fails, it will be verified several times, and it may pass later. " A black seller said that stealing other people’s informationAPPAccount registration and verification is illegal, and the state has cracked down hard, so I only sell software and teaching, and I won’t directly operate it.
According to the tip of the black seller, the Beijing News reporter spent500Yu Yuan bought an Android phone and a set of dynamic processing software and teaching, which were attached by the black seller.30Set of photos of the front and back of the ID card and the photo of the hand-held ID card.
In the actual experience process, according to the seller of black products, use a brand that has been brushed.R9Mobile phone, save the processed face dynamic video on this mobile phone and open it.APPIf you cover the camera with objects and make the camera in a black screen state, you can successfully pass the security verification.
The Beijing News reporter used this method and passed the face recognition on the platforms of exploration and Zhaopin recruitment.
The customer service staff told the Beijing News reporter that if personal identity information is found to be stolen, it can only be reflected to the platform after the user finds it. After that, the user needs to provide his identity information to the platform for review. After the review is passed, the platform will ban the authenticated account. They will give feedback on the vulnerability of face recognition authentication on the exploration platform.
The customer service staff of Zhaopin, Momo and other platforms all said that there is no good response to false face recognition at present, and the situation will be fed back later.
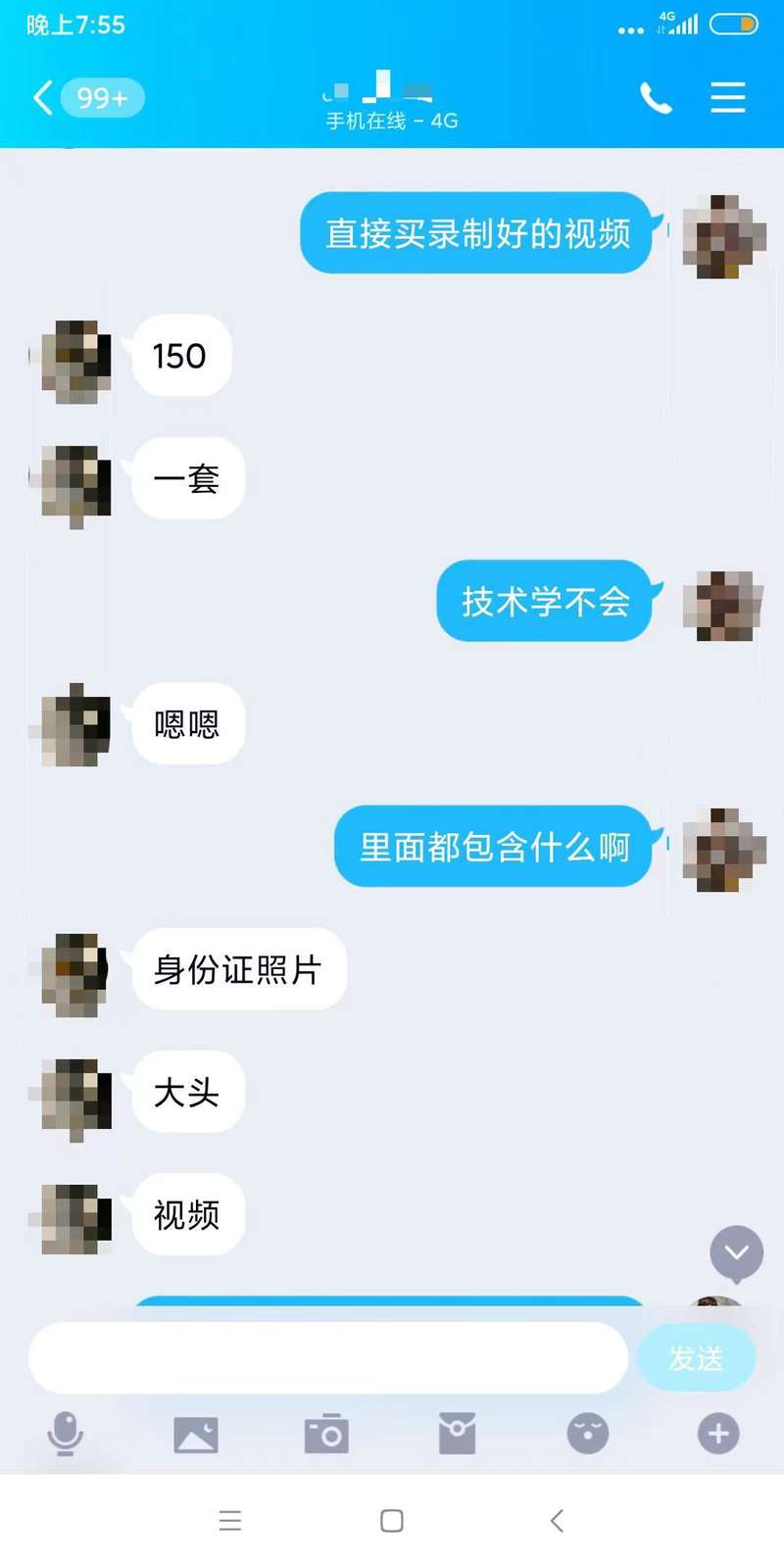
A black vendor sells real-life face recognition videos and bids for a set of 150 yuan. screenshot
Lawyer: It is illegal to sell face information privately.
There are many cases in which personal information is illegally used after being sold.
On the China refereeing document online, a criminal judgment about face recognition verification shows that from2018yearsevenSince January, defendants Zhang, Yu and others have used their personal identity information to register Alipay accounts for the purpose of making profits, and used software to make photos of citizens’ heads into citizens.3DAvatar, so as to pass Alipay face recognition authentication.
In this way, you can get the corresponding red envelope rewards (including the red envelope for inviting newcomers, the red envelope for general consumption, the red envelope for flowers, etc.) provided by Alipay for inviting new Alipay users, and each newly registered Alipay can at least get it.28Yuan income. As of the time of the incident, the gang illegally collected nearly2000Ten thousand pieces of citizenship information, using the personal identity information of others, successfully registered at least547A real-name Alipay account that has passed face recognition authentication, making a profit.fourTen thousand yuan.
Zhao Zhanling, a lawyer of Beijing Yunjia Law Firm, said that facial feature information of a person can directly identify the true identity of a specific natural person, which belongs to the category of personal information. It is illegal or even criminal to buy and sell personal information without the consent of the user.
According to the provisions of the Civil Code, citizens enjoy civil rights to personal information, and illegally collecting and selling other people’s information without their consent will constitute civil infringement. In addition, the Criminal Law Amendment IX stipulates the crime of infringing citizens’ personal information. Buying and selling highly sensitive personal information reaches a certain amount, which meets the criteria for filing a case stipulated in the judicial interpretation of the two courts. In this process, both the buyer and the seller are suspected of violating citizens’ personal information.
After the personal information of a natural person is illegally bought and sold by others, it is used for some illegal or even criminal acts, so he does not bear legal responsibility for it. However, proof is needed to prove that personal information was illegally obtained and stolen by others. There are many criminal cases concerning personal information, and public security organs arrest a large number of criminal suspects who infringe citizens’ personal information every year.
Beijing News reporter Liu Mingyang
Editor gan Hao
Proofread Junyan Zhang